Continuing the discussion from Google Officially Launches the Google TV Streamer:
@Tech2 to be clear, I would not characterize it the way you said. It was very late last night and I was engineering a solution on the fly using tools and commands I’ve never seen before, so I apologize if my explanation was lacking. Let me try again:
-
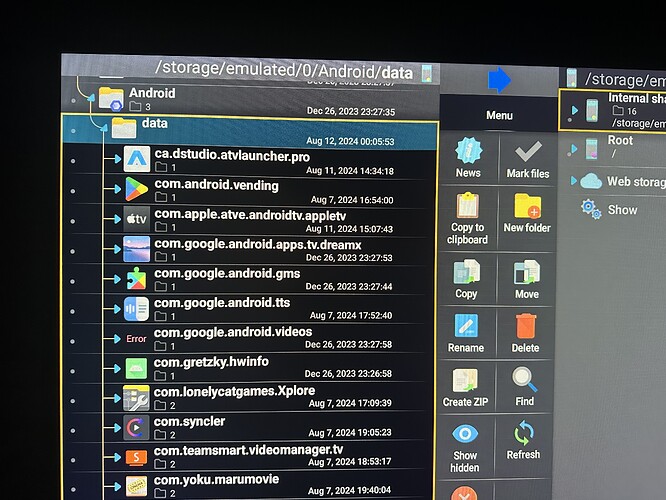
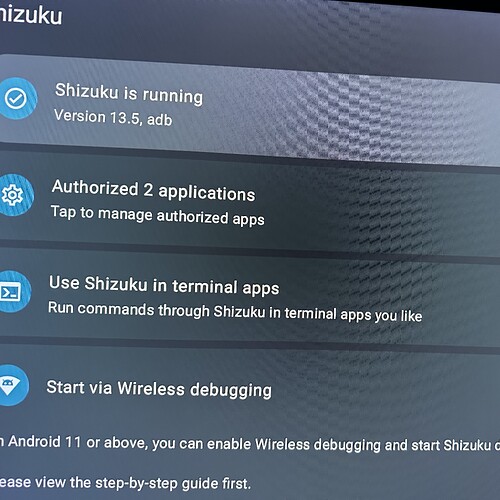
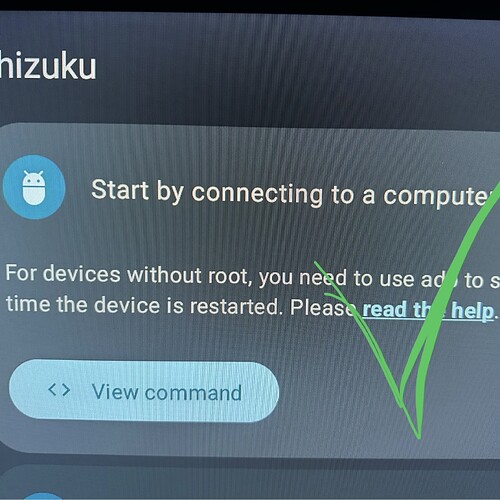
The app X-plore utilizes functions from of an API functionality of an app called Shizuku, which is an AWESOME and relatively new library that remarkably is able to execute elevated system commands as a regular non-elevated user. Basically, these developers have found a way to do things in various Android based operating systems that had previously been blocked for standard users. Things that normally require being an admin or “rooting” the device can now be done using Shizuku and without rooting the device. BTW, when I say “rooting” I’m not talking about what this community calls “jail breaking” which is actually just turning on a feature provided by the developer. I’m talking about getting true root level access which is hacking the code to obtain access the developer tries to withhold. Now, for certain, the Shizuku APIs are not able to obtain true superuser level access, but they do allow us to access many elevated functions rather safely and easily; plus, as it is open source, basically EVERYONE developing apps right now is finding ways to include it in their products.
-
Also, to be clear, BOTH the Shield and Onn devices are running versions of AndroidTV that lock down the “DATA” directory in which you wanted access. The Shield’s data directory is a little less restrictive than the Onn’s because it is using an older version of AndroidTV as its baseline. AFAIK Nvidia didn’t do anything to purposefully make it less restrictive, they just stopped updating their software 
-
X-plore is one such application that is now leveraging these the Shizuku APIs, and I would bet Kodi does too… or will have to soon.
-
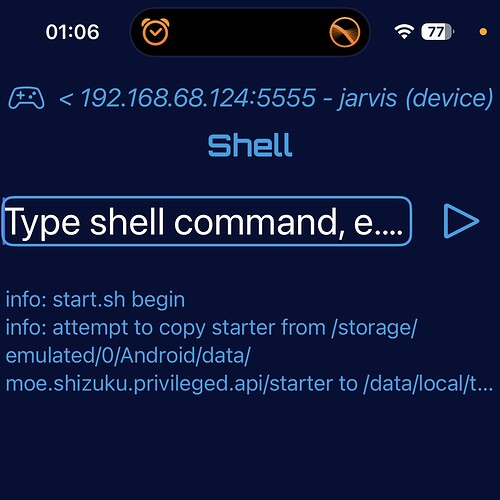
In order to access the data directory on the Shield using X-Plore, I had to follow the instructions in the X-plore documentation to execute Shizuku in a very specific way that made use of other side-loaded apps (mouse, etc.) and some technical know how on my part. It took me about 3 tries to get the commands correct on my Shield before I gained access to the data directory; however, I don’t run Kodi and that’s an important distinction here, because if you were to go buy a new, up to date Shield right now without installing anything or running any ADB shell commands, you would 100% be locked out of that data directory too. In fact I just did a quick search and the first link proved my point: to get Kodi access to the data directory you must bypass the Android/Shield build-in security restrictions.
The bottom line:
- Both devices restrict access to those directories.
** X-Plore bundles the Shizuku APIs within its app.
*** The Shield’s older ATV9 has OS level restrictions that tried to stop X-Plore from executing the Shizuku commands that give access to the directories which forced me to use my technical knowhow and other side-loaded apps get the Shizuku commands successfully executed. Alternatively, instead of using Shizuku to gain access to the directories, you can instead side-load an app and run ADB commands to do the same thing.
**** The Onn’s newer ATV11 has an extra OS level restrictions that tried to stop X-Plore from executing the Shizuku commands, but there’s a simple workaround by side-loading the Shizuku app first and running with an ADB shell command, then the Shizuku commands successfully executed.
That was a bunch of words just to say:
But OS’s block restrict access to the directors directories, but also in both cases there’s a simple workaround of side-loading an app and running some ADB commands.
The over difference really is that you had the Shield procedure already laid out for you and I had to completely invent my solution, but I could write up the same solution for you and then you could run it just as easily.
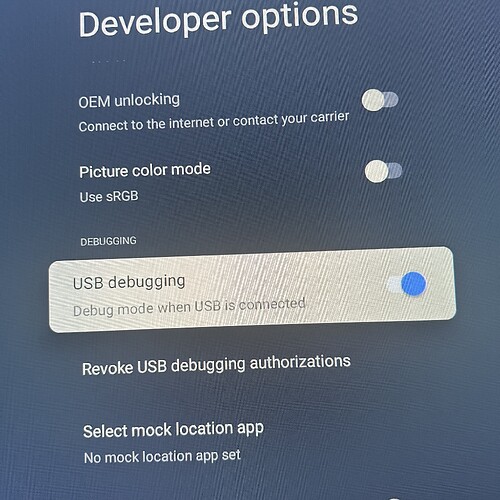
To the last point, I was too tired to finish last night, so right now every time a reboot my device I have to run a single, quick ADB command which I can do from my one in under 30 seconds, but I’ve already searched and found multiple write-ups on how to get the command to run automatically at boot, so I expect once I find and implement that last step, it will be 100% hands free just like on the shield.
Does this make it clearer? I hope I’ve been helpful!!!
Let me know if there’s any questions @Miki and @Tech2 !!